Tweetovi
- Tweetovi, trenutna stranica.
- Tweetovi i odgovori
- Medijski sadržaj
Blokirali ste korisnika/cu @ducnt_
Jeste li sigurni da želite vidjeti te tweetove? Time nećete deblokirati korisnika/cu @ducnt_
-
Prikvačeni tweet
My first `double kill` at
@wordpressdotcom: https://nvd.nist.gov/vuln/detail/CVE-2019-16780 … https://nvd.nist.gov/vuln/detail/CVE-2019-16781 … https://wordpress.org/news/2019/12/wordpress-5-3-1-security-and-maintenance-release/ … Kudos to WordPress security team with very quickly and awesome work Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi
Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi -
Nguyen The Duc proslijedio/la je Tweet
Neatly bypassing Content Security Policy. Why 'unsafe-inline' is almost always a full-fledged XSS. https://lab.wallarm.com/how-to-trick-csp-in-letting-you-run-whatever-you-want-73cb5ff428aa …
#XSSPrikaži ovu nitHvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi -
Nguyen The Duc proslijedio/la je Tweet
DOM Clobbering strikes back by
@garethheyeshttps://portswigger.net/research/dom-clobbering-strikes-back …Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi -
Nguyen The Duc proslijedio/la je Tweet
Thanks to
@MDSecLabs research, new stuff are being released for http://ysoserial.net soon - as for the features, payload minimization, raw cmd command, and auto command encoding within JSON/XML messages are being released after the PR review by@pwntesterHvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi -
Nguyen The Duc proslijedio/la je TweetHvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi
-
Nguyen The Duc proslijedio/la je TweetHvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi
-
Nguyen The Duc proslijedio/la je Tweet
Here's my write-up for
#h1415’s CTF challenge! https://lbherrera.github.io/lab/h1415-ctf-writeup.html …Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi -
Nguyen The Duc proslijedio/la je Tweet
CVE-2020-7471: SQLI in Django: django.contrib.postgres.aggregates.StringAgg aggregation function was subject to SQL injection, using a suitably crafted delimiter. https://djangoproject.com/weblog/2020/feb/03/security-releases/ … FIX: https://github.com/django/django/commit/eb31d845323618d688ad429479c6dda973056136 …pic.twitter.com/NljqLmin93
 Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi
Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi -
Nguyen The Duc proslijedio/la je Tweet
@ngalongc,@EdOverflow, and I are starting a new security blog. In our first write-up, we will discuss the impact of "SameSite by default" and how it affects web app sec. Feel free to request future topics you would like us to cover. https://blog.reconless.com/samesite-by-default/ …pic.twitter.com/5R23YmpksT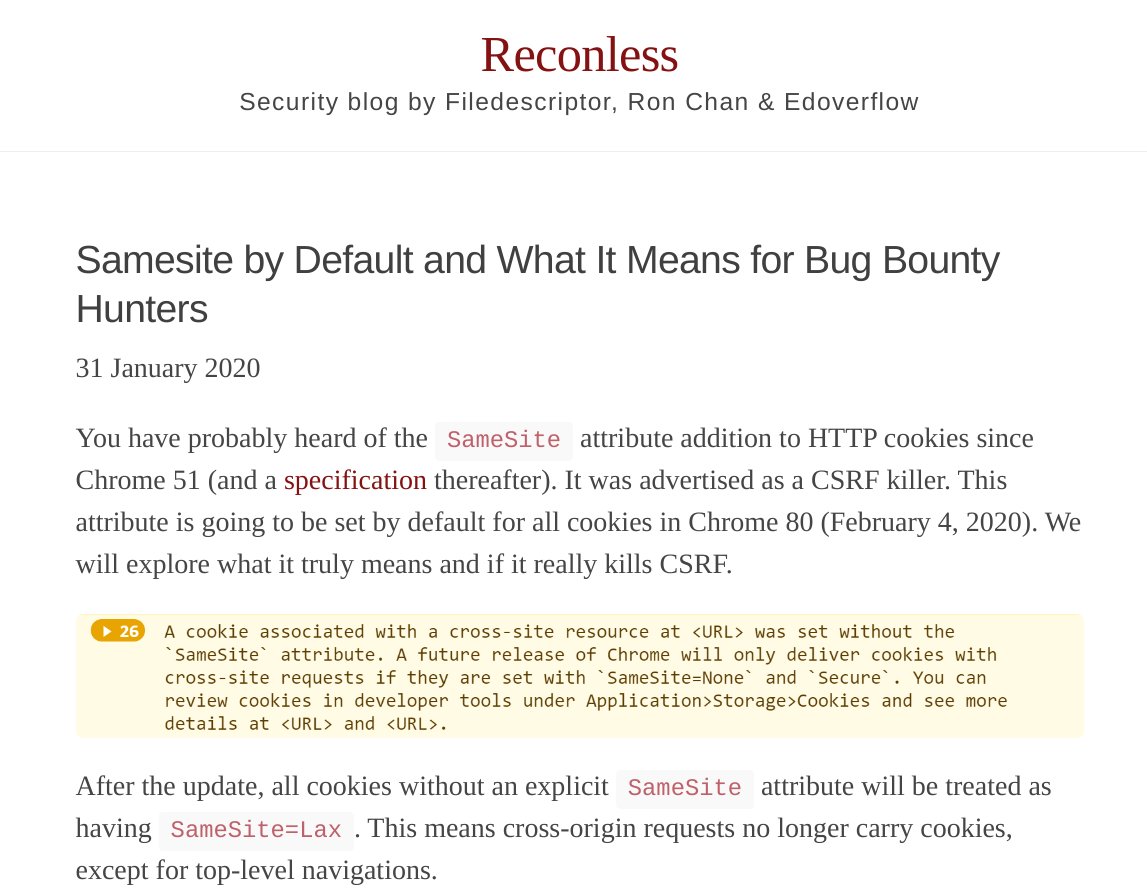 Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi
Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi -
Nguyen The Duc proslijedio/la je Tweet
Someone dropped a PHP zero-day on GitHub. Talked to the PHP team last night. Bug requires local foothold to exploit, so not usable for remote attacks. Also, this is the second exploit for this "disable_functions bypass" in the last few months. https://github.com/mm0r1/exploits/tree/master/php7-backtrace-bypass …pic.twitter.com/MAWD8FpBRx
 Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi
Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi -
Nguyen The Duc proslijedio/la je Tweet
.Net being open-source makes tracking these things cool. I just hope GitHub adds code navigation support for .net code soon as well. credit for the bug goes to
@irsdl of course.https://github.com/dotnet/wpf/pull/2428/commits/eeb2a5ee95617c171b8051632e6454235f8bee14 …Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi -
Nguyen The Duc proslijedio/la je Tweet
Also for the iPhone 11 Pro Max, iOS 13.3.1 beta3 Jailbreakpic.twitter.com/0RVjhcyOAr
Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi -
Nguyen The Duc proslijedio/la je Tweet
Here are my (updated) slides from
@AppSecCali for my talk "Owning The Cloud Through SSRF & PDF Generators" with Chris Holt from@TheParanoids. Big thank you to@daeken,@bbuerhaus,@infosec_au ,@orange_8361,@Alyssa_Herrera_, and@hacker_ ! https://docs.google.com/presentation/d/1vMbvg05euZdq1wDxtR04EvC6iBiyIbcFeRAHWr1McdA/edit#slide=id.g6f82de3c45_0_9 …pic.twitter.com/q3UwhtzfbE Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi
Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi -
Nguyen The Duc proslijedio/la je Tweet
RDP Vuln
#BlueGate CVE-2020-0609 & CVE-2020-0610 RD Gateway PoC (DoS) by@ollypwn https://github.com/ollypwn/BlueGate … Scanner by@MalwareTechBloghttps://github.com/MalwareTech/RDGScanner …Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi -
Nguyen The Duc proslijedio/la je Tweet
The Bezos forensic report is not very good. The forensic analysis should be done by
@citizenlab who at least have the relevant experience. The MP4 file should contain the exploit (if it is CVE-2019-11931). The exploit trigger should be visible with ffmpeg https://processors.wiki.ti.com/index.php/Extracting_MPEG-4_Elementary_Stream_from_MP4_Container#Extract_Elementary_Stream_with_FFmpeg …Prikaži ovu nitHvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi -
Nguyen The Duc proslijedio/la je Tweet
This is a pretty good reminder that any invasive heuristics in the browser - be it XSS filters or privacy protections - often cause more problems than they address: https://arxiv.org/ftp/arxiv/papers/2001/2001.07421.pdf …
Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi -
Nguyen The Duc proslijedio/la je Tweet
Learn how an authenticated RCE vulnerability in
#WordPress < 5.2.4 allows attackers to bypass hardening mechanisms. Read more -> http://bit.ly/3aspShs#vulnerability#php#cmspic.twitter.com/UmbAHzH9MB Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi
Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi -
Nguyen The Duc proslijedio/la je Tweet
Just published a blog post talking about some iOS kernel framebuffer research I’ve been looking at over the last couple weeks. Have a read if you’re interested :)https://link.medium.com/3155zMpgm3
Prikaži ovu nitHvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi -
Nguyen The Duc proslijedio/la je Tweet
RDP to RCE: When Fragmentation Goes Wrong AKA: What we know about CVE-2020-0609 and CVE-2020-0610.https://www.kryptoslogic.com/blog/2020/01/rdp-to-rce-when-fragmentation-goes-wrong/ …
Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi -
Nguyen The Duc proslijedio/la je Tweet
"CVE-2020-0601: the ChainOfFools attack explained with PoC" https://research.kudelskisecurity.com/2020/01/15/cve-2020-0601-the-chainoffools-attack-explained-with-poc/ …
#cve#pocHvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi -
Nguyen The Duc proslijedio/la je Tweet
CVE-2020-5504 SQLI in phpMyAdmin: A malicious user could inject custom SQL in place of their own username when creating queries to this page https://www.phpmyadmin.net/security/PMASA-2020-1/ … fix: https://github.com/phpmyadmin/phpmyadmin/commit/c86acbf3ed49f69cf38b31879886dd5eb86b6983 …pic.twitter.com/S3a3B1zHz4

 Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi
Hvala. Twitter će to iskoristiti za poboljšanje vaše vremenske crte. PoništiPoništi
Čini se da učitavanje traje već neko vrijeme.
Twitter je možda preopterećen ili ima kratkotrajnih poteškoća u radu. Pokušajte ponovno ili potražite dodatne informacije u odjeljku Status Twittera.






















