你已封鎖 @ducnt_
你確定要查看這些推文嗎?查看推文並不會將 @ducnt_ 解除封鎖
-
釘選的推文
My first `double kill` at
@wordpressdotcom: https://nvd.nist.gov/vuln/detail/CVE-2019-16780 … https://nvd.nist.gov/vuln/detail/CVE-2019-16781 … https://wordpress.org/news/2019/12/wordpress-5-3-1-security-and-maintenance-release/ … Kudos to WordPress security team with very quickly and awesome work 謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原
謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原 -
Filed a duplicate with gr8 bug was found by
@SecurityMB but can reopen it with a triaged issue. Really a excited moment.#bugbountytippic.twitter.com/iI1mSCfNLC

 謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原
謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原 -
Nguyen The Duc 已轉推
New blog post! Here is how you can use MSBuild’s UnregisterAssembly task to execute arbitrary code in a .NET assembly.

#cybersecurity#infosec@subTee@BHinfoSecurityhttps://bit.ly/2PmChuz謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原 -
Nguyen The Duc 已轉推
Just wrote a new article about how I found a Remote Command Execution 0-day (CVE-2020-8813) via static analysis in Cacti v1.2.8 the popular infrastructure graphing solution. I also explained how to exploit it without authentication in some cases.https://shells.systems/cacti-v1-2-8-authenticated-remote-code-execution-cve-2020-8813/ …
謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原 -
Nguyen The Duc 已轉推
Slides from my
#OffensiveCon20 talk on iMessage exploitation: https://saelo.github.io/presentations/offensivecon_20_no_clicks.pdf … More technical details in the blog post: https://googleprojectzero.blogspot.com/2020/01/remote-iphone-exploitation-part-1.html … Great conference again, thanks@offensive_con team! :)謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原 -
Nguyen The Duc 已轉推
[PoC] CVE-2020-0618 Microsoft SQL Server Reporting Services RCE Vulnerability POST /ReportServer/pages/ReportViewer.aspx HTTP/1.1 Host: target ... ... NavigationCorrector$PageState=NeedsCorrection&NavigationCorrector$ViewState=[PayloadHere]&__VIEWSTATE= https://github.com/euphrat1ca/CVE-2020-0618 …pic.twitter.com/FeCBMcnaPv
此媒體可能含有敏感內容。 了解更多 謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原
謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原 -
Nguyen The Duc 已轉推
Just published another remote code execution chain I exploited recently. I also wrote about how organizations can stop these attacks at the development stage - the key is convention over configuration.https://spaceraccoon.dev/a-tale-of-two-formats-exploiting-insecure-xml-and-zip-file-parsers-to-create-a …
謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原 -
Nguyen The Duc 已轉推
@Jxck_ さんとSpectreやXS-LeaksやCross-Origin-*ヘッダーについて話しました! / ep63 Cross Origin Info Leakshttps://mozaic.fm/episodes/63/cross-origin-info-leaks.html …顯示此對話串謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原 -
Nguyen The Duc 已轉推
Top 10 new web hacking techniques of 2019https://portswigger.net/research/top-10-web-hacking-techniques-of-2019 …
謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原 -
Nguyen The Duc 已轉推
I've discovered logic privilege escalation bug on AMD User Experience Program Launcher from Radeon Software https://github.com/sailay1996/amd_eop_poc … https://heynowyouseeme.blogspot.com/2020/02/privilege-escalation-filewrite-eop-in.html … https://heynowyouseeme.blogspot.com/2020/02/another-privilege-escalation-filewrite.html …
#privilege_escalation#CVE-2020-8950pic.twitter.com/WdnklR3vGu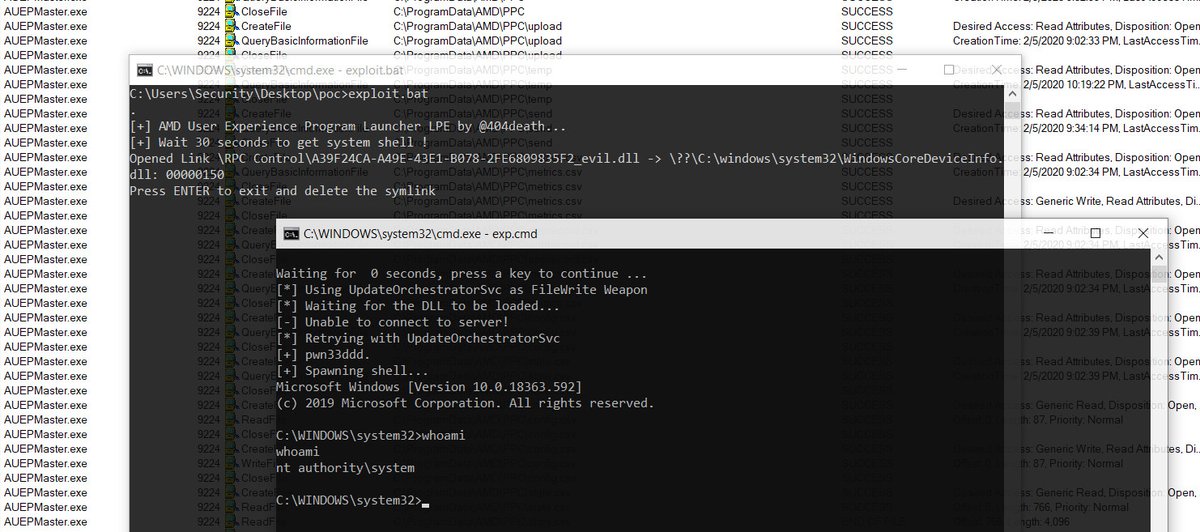 謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原
謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原 -
Nguyen The Duc 已轉推
Blind SSRF exploitation En: https://lab.wallarm.com/blind-ssrf-exploitation/ … Ru: https://bo0om.ru/blind-ssrf What about port scanning using DNS-requests?pic.twitter.com/R9DEt7HSmP
謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原 -
Nguyen The Duc 已轉推
A few small proposals for PHP 8 have been accepted:
$object::class https://wiki.php.net/rfc/class_name_literal_on_object … Static return type https://wiki.php.net/rfc/static_return_type … Variable syntax tweaks https://wiki.php.net/rfc/variable_syntax_tweaks …謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原 -
Nguyen The Duc 已轉推
Neatly bypassing Content Security Policy. Why 'unsafe-inline' is almost always a full-fledged XSS. https://lab.wallarm.com/how-to-trick-csp-in-letting-you-run-whatever-you-want-73cb5ff428aa …
#XSS顯示此對話串謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原 -
Nguyen The Duc 已轉推
DOM Clobbering strikes back by
@garethheyeshttps://portswigger.net/research/dom-clobbering-strikes-back …謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原 -
Nguyen The Duc 已轉推
Thanks to
@MDSecLabs research, new stuff are being released for http://ysoserial.net soon - as for the features, payload minimization, raw cmd command, and auto command encoding within JSON/XML messages are being released after the PR review by@pwntester謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原 -
Nguyen The Duc 已轉推謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原
-
Nguyen The Duc 已轉推謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原
-
Nguyen The Duc 已轉推
Here's my write-up for
#h1415’s CTF challenge! https://lbherrera.github.io/lab/h1415-ctf-writeup.html …謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原 -
Nguyen The Duc 已轉推
CVE-2020-7471: SQLI in Django: django.contrib.postgres.aggregates.StringAgg aggregation function was subject to SQL injection, using a suitably crafted delimiter. https://djangoproject.com/weblog/2020/feb/03/security-releases/ … FIX: https://github.com/django/django/commit/eb31d845323618d688ad429479c6dda973056136 …pic.twitter.com/NljqLmin93
 顯示此對話串謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原
顯示此對話串謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原 -
Nguyen The Duc 已轉推
@ngalongc,@EdOverflow, and I are starting a new security blog. In our first write-up, we will discuss the impact of "SameSite by default" and how it affects web app sec. Feel free to request future topics you would like us to cover. https://blog.reconless.com/samesite-by-default/ …pic.twitter.com/5R23YmpksT 謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原
謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原 -
Nguyen The Duc 已轉推
Someone dropped a PHP zero-day on GitHub. Talked to the PHP team last night. Bug requires local foothold to exploit, so not usable for remote attacks. Also, this is the second exploit for this "disable_functions bypass" in the last few months. https://github.com/mm0r1/exploits/tree/master/php7-backtrace-bypass …pic.twitter.com/MAWD8FpBRx
 謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原
謝謝,Twitter 將使用這項資訊來使你的時間軸更完美。 還原還原
看來要一段時間讀取資料。
Twitter 可能已超出負載,或發生暫時性的小問題。請再試一次,或造訪 Twitter 狀態以取得更多資訊。



















