Tweets
- Tweets, page courante.
- Tweets & réponses
- Médias
Vous avez bloqué @ducnt_
Êtes-vous sûr de vouloir voir ces Tweets ? Les voir ne débloquera pas @ducnt_
-
Tweet épinglé
I really happy to share an article that bypass Akamai web application firewall and exploit a SQL Injection vulnerability. Hope this article will help someone in the same situation :).
#bugbountytips#bypass#bounty https://hackemall.live/index.php/2020/03/31/akamai-web-application-firewall-bypass-journey-exploiting-google-bigquery-sql-injection-vulnerability/ …Afficher cette discussionMerci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer -
Nguyen The Duc a retweeté
No Thanks , We need Bounties only







#hackerone#bugcrowd#bugbouunty@Hacker0x01@Bugcrowd#bugbountymemespic.twitter.com/5bOuogqGqD Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer
Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer -
Nguyen The Duc a retweeté
The
@Firefox fuzzing team has been developing a new fuzzer to help identify security vulnerabilities in the implementation of WebAPIs in Firefox. This fuzzer, which we’re calling Domino, leverages the WebAPIs’ own WebIDL definitions as a fuzzing grammar.https://hacks.mozilla.org/2020/04/fuzzing-with-webidl/ …Afficher cette discussionMerci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer -
Nguyen The Duc a retweeté
Detailing CVE-2020-0932 - a now patched RCE bug in
#Microsoft#SharePoint reported to us by an anonymous researcher. The blog lays out how code exec is possible using TypeConverters and provides video demonstration and PoC. Read the post athttps://bit.ly/3cVGRt1Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer -
Nguyen The Duc a retweeté
Releasing another side-project: CursedChrome. A Chrome-extension implant that turns victim Chrome browsers into HTTP proxies. Using these proxies you can browse the web authenticated as your victims for all of their websites. Setup takes only 5-10 mins
 https://github.com/mandatoryprogrammer/CursedChrome …pic.twitter.com/Y8VRAEXon0
https://github.com/mandatoryprogrammer/CursedChrome …pic.twitter.com/Y8VRAEXon0
 Afficher cette discussionMerci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer
Afficher cette discussionMerci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer -
Nguyen The Duc a retweeté
We’ve just published SitRep, our host triage tool developed by
@two06. It brings extensibility and OpSec considerations to the triage process: https://github.com/mdsecactivebreach/sitrep/blob/master/README.md …pic.twitter.com/krIQEwTQWx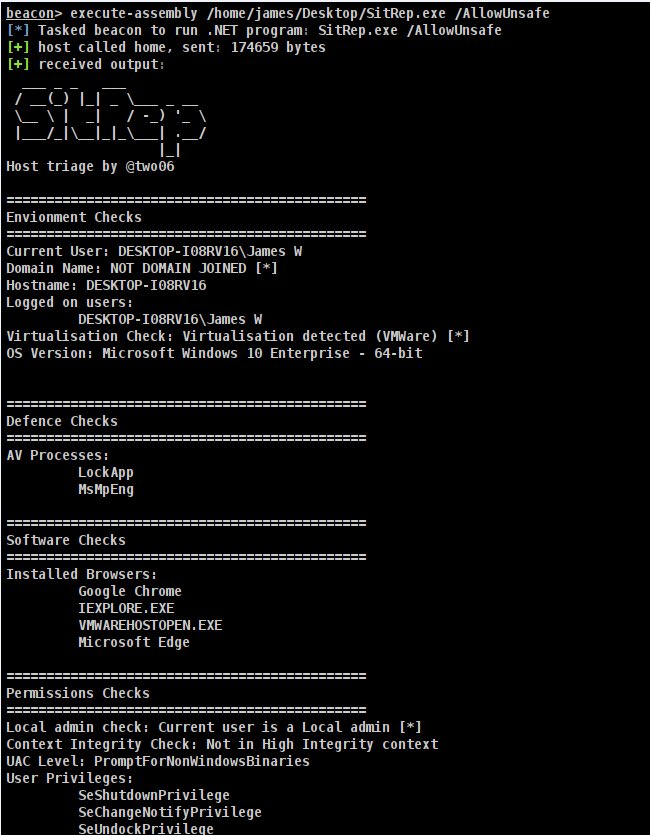 Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer
Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer -
Nguyen The Duc a retweeté
Check out my write-up about an account takeover vulnerability I found in Microsoft Teams. By sending a GIF, you could get access to the user's data and "ultimately take over an organization's entire roster of Teams accounts". https://www.cyberark.com/threat-research-blog/beware-of-the-gif-account-takeover-vulnerability-in-microsoft-teams/ …pic.twitter.com/2xGLuzwygK
Afficher cette discussionMerci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer -
Nguyen The Duc a retweeté
Exploit Proof-of-Concept for CVE-2020-12138, Privilege Escalation in ATI Technologies Inc. driver 'atillk64.sys'. Thanks to all those cited for helping me along the way.https://h0mbre.github.io/atillk64_exploit/# …
Afficher cette discussionMerci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer -
Nguyen The Duc a retweeté
#DNS support added and pushed to#nuclei master, go and automate all the takeovers and DNS related detections and vulnerabilities. We also updated guide document with DNS request template information https://github.com/projectdiscovery/nuclei-templates/blob/master/GUIDE.md#dns-requests …#bugbounty#dns#security#pentestpic.twitter.com/fogdF2nD9R Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer
Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer -
Nguyen The Duc a retweeté
Slides for "Attacking Secondary Contexts in Web Applications" -https://docs.google.com/presentation/d/1N9Ygrpg0Z-1GFDhLMiG3jJV6B_yGqBk8tuRWO1ZicV8/edit?usp=sharing …
Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer -
Nguyen The Duc a retweeté
http://ysoserial.net v1.33 released with a ton of new features. Thanks to
@irsdl for the great PRs! You can see whats new here https://www.mdsec.co.uk/2020/04/introducing-ysoserial-net-april-2020-improvements/ …Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer -
Nguyen The Duc a retweeté
New blog post: CVE-2020-0022 an Android 8.0-9.0 Bluetooth Zero-Click RCE – BlueFraghttps://insinuator.net/2020/04/cve-2020-0022-an-android-8-0-9-0-bluetooth-zero-click-rce-bluefrag/ …
Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer -
Nguyen The Duc a retweeté
In his first
@MDSecLabs blog post,@jfmeee explains how to abuse@firefox in enterprise environments https://www.mdsec.co.uk/2020/04/abusing-firefox-in-enterprise-environments/ …pic.twitter.com/wxKSfIHEHi Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer
Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer -
Nguyen The Duc a retweeté
CVE-2020-7066 is a pretty neat SSRF vector in PHP; URL parsing differences strike yet again.pic.twitter.com/Gj28eSkC4e
 Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer
Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer -
Nguyen The Duc a retweeté
My writeup for the haproxy http2 bug (CVE-2020-11100) is now public: https://bugs.chromium.org/p/project-zero/issues/detail?id=2023 …. Includes a PoC exploit to demonstrate RCE against Ubuntu 19.10.
Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer -
Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer
-
Nguyen The Duc a retweeté
This is a simple story about how to control back to web app from SQL with http://ASP.NET SessionState deserialization (article only in Traditional Chinese)https://cyku.tw/from-sql-to-rce-exploit-aspnet-app-with-sessionstate/ …
Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer -
Nguyen The Duc a retweeté
It's here! Details on how we achieved
#SMBGhost RCE are available. Enjoy! "I'll ask your body": SMBGhost pre-auth RCE abusing Direct Memory Access structs by (@hugeh0ge)https://ricercasecurity.blogspot.com/2020/04/ill-ask-your-body-smbghost-pre-auth-rce.html …Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer -
Nguyen The Duc a retweetéMerci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer
-
Nguyen The Duc a retweeté
New write up - "Abusing HTTP Path Normalization and Cache Poisoning to steal Rocket League accounts" https://samcurry.net/abusing-http-path-normalization-and-cache-poisoning-to-steal-rocket-league-accounts/ …pic.twitter.com/n5dl0fmpqK
 Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer
Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer -
Nguyen The Duc a retweeté
POC: http://localhost:8000/test/?q=20) = 1 OR (select utl_inaddr.get_host_name((SELECT version FROM v%24instance)) from dual) is null%20 OR (1%2B1 analysis: https://xz.aliyun.com/t/7403 https://twitter.com/chybeta/status/1235176376321183744 …pic.twitter.com/D5mZPu6qtR
 Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer
Merci. Twitter en tiendra compte pour améliorer votre fil. SupprimerSupprimer
Le chargement semble prendre du temps.
Twitter est peut-être en surcapacité ou rencontre momentanément un incident. Réessayez ou rendez-vous sur la page Twitter Status pour plus d'informations.


 | Security Researcher | Sr. Security Engineer | CTF player
| Security Researcher | Sr. Security Engineer | CTF player 


















