Tweet
- Tweet, halaman saat ini.
- Tweet & balasan
- Media
Anda memblokir @ducnt_
Yakin ingin melihat Tweet ini? Melihat Tweet tidak akan membuka blokir @ducnt_
-
Tweet Sematan
I really happy to share an article that bypass Akamai web application firewall and exploit a SQL Injection vulnerability. Hope this article will help someone in the same situation :).
#bugbountytips#bypass#bounty https://hackemall.live/index.php/2020/03/31/akamai-web-application-firewall-bypass-journey-exploiting-google-bigquery-sql-injection-vulnerability/ …Tampilkan utas iniTerima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan -
Nguyen The Duc me-RetweetTerima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan
-
Nguyen The Duc me-Retweet
Cross origin access with exception object + full exploit (reward: $25633) https://crbug.com/453937
Terima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan -
Nguyen The Duc me-Retweet
Last month, I found a DOM XSS that led to RCE in
@moodle. Here is the write-up: https://cube01.io/blog/Moodle-DOM-Stored-XSS-to-RCE.html … Most of the credit goes to@SecurityMBpic.twitter.com/LKboLLVs0C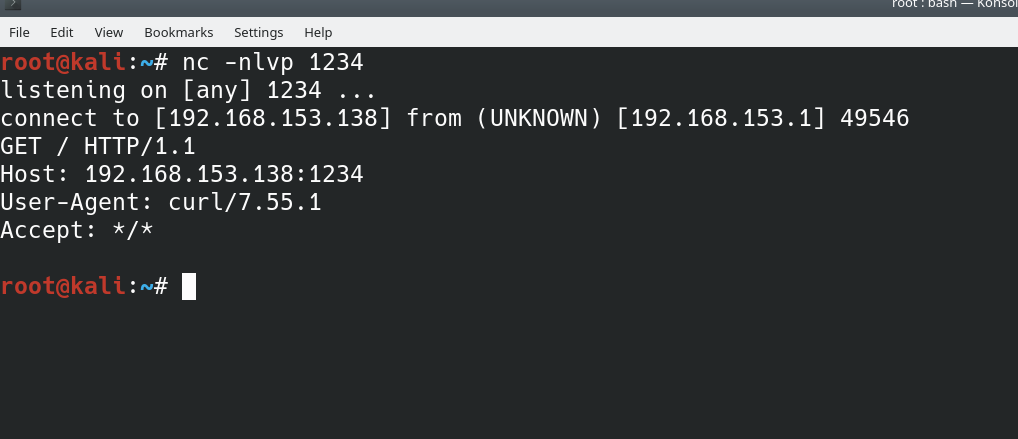 Tampilkan utas iniTerima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan
Tampilkan utas iniTerima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan -
Nguyen The Duc me-Retweet
An impossible lab has been solved! Congratulations to
@wcbowling who solved the attribute context arbitrary code lab. With the following solution: ?a=`+alert(document.domain);//&x=%22oncut=%22eval(%27`%27%2bURL)' the length limit has now been reduced to 20.Terima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan -
Nguyen The Duc me-Retweet
Abusing Microsoft Outlook 365 to Capture NTLMhttps://www.hackingarticles.in/abusing-microsoft-outlook-365-to-capture-ntlm/ …
Terima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan -
Nguyen The Duc me-Retweet
SSRF + CRLF + HTTP Pipeline + Docker API = RCE… How dangerous is Request Splitting, a vulnerability in Golang or how we found the RCE in Portainer and hacked Uberhttps://link.medium.com/dSWQ6ewPL6
Terima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan -
Nguyen The Duc me-Retweet
Thanks Safari :D XSS via hash is back!! https://twitter.com/PortSwiggerRes/status/1263853351172804612 …pic.twitter.com/GqsRsrXJkr
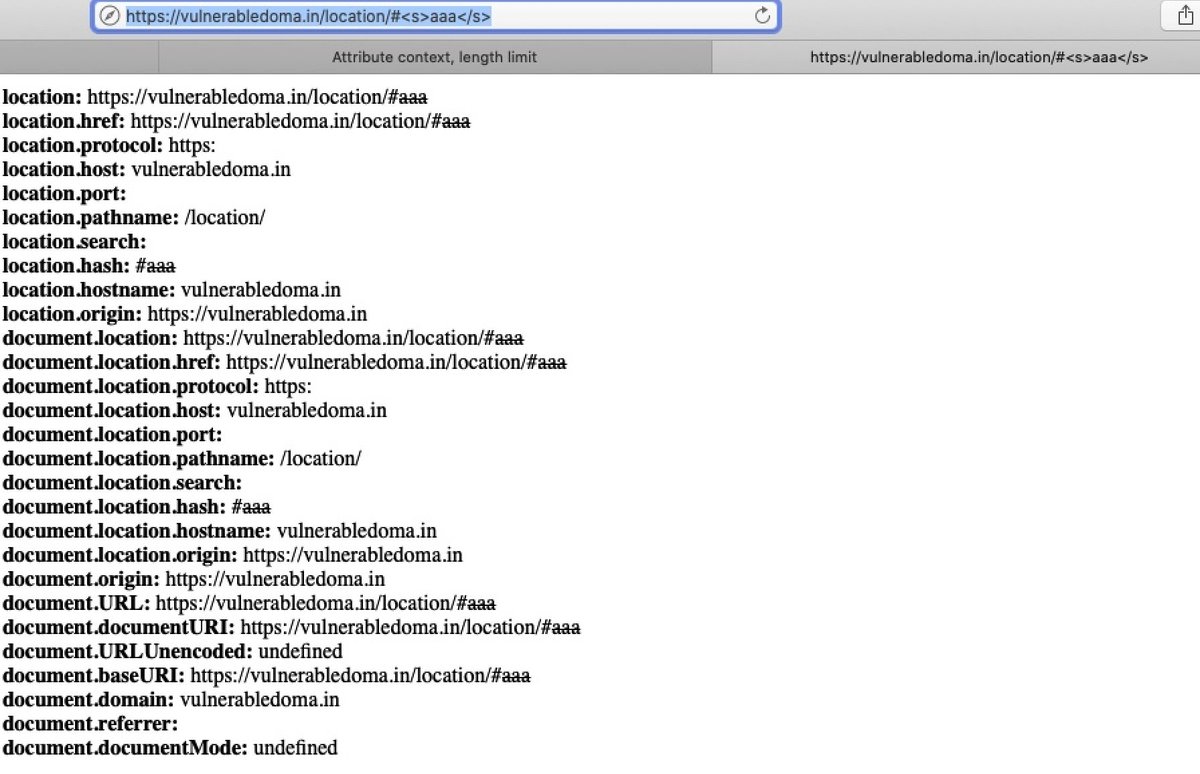 Terima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan
Terima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan -
Nguyen The Duc me-RetweetTerima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan
-
Nguyen The Duc me-Retweet
CVE-2020-9484 Tomcat RCE漏洞分析 https://mp.weixin.qq.com/s/OGdHSwqydiDqe-BUkheTGg …
Terima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan -
Nguyen The Duc me-Retweet
Here is a write-up of a very interesting RCE bug I found on Google Cloud Deployment Manager for the
@GoogleVRP: https://www.ezequiel.tech/2020/05/rce-in-cloud-dm.html …Terima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan -
Nguyen The Duc me-Retweet
Aerial ‘smoke screen’ used to protect ships in battle in the 20th century.pic.twitter.com/6ZlpL57iH8
Terima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan -
Nguyen The Duc me-Retweet
I blogged about some interesting behavior which lead to an internal auth bypass. Smuggling HTTP headers through reverse proxies: https://telekomsecurity.github.io/2020/05/smuggling-http-headers-through-reverse-proxies.html …
Tampilkan utas iniTerima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan -
Nguyen The Duc me-Retweet
Increasing disk and memory size make Integer Overflow great again
 https://twitter.com/julianor/status/1262806932198432768 …Terima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan
https://twitter.com/julianor/status/1262806932198432768 …Terima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan -
Nguyen The Duc me-Retweet
Text fragments will soon be available in Chromium land. You can then use `#:~:text=` to highlight certain text.

 Chrome status: https://chromestatus.com/feature/4733392803332096 …
Chrome status: https://chromestatus.com/feature/4733392803332096 …
 Spec: https://wicg.github.io/ScrollToTextFragment/ …
Spec: https://wicg.github.io/ScrollToTextFragment/ …
#devsheets Video alt: Usage of text fragments to highlight text on wikipediapic.twitter.com/W5tUYZk8NYTampilkan utas iniTerima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan -
Nguyen The Duc me-Retweet
 Google open sourced their fuzzing dictionaries!
https://github.com/google/fuzzing/tree/master/dictionaries …Terima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan
Google open sourced their fuzzing dictionaries!
https://github.com/google/fuzzing/tree/master/dictionaries …Terima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan -
Nguyen The Duc me-Retweet
DEFCON web solution (except grad school)https://gist.github.com/stypr/369141278c186b9cffbeec68fe1b5d2e …
Tampilkan utas iniTerima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan -
Nguyen The Duc me-Retweet
I made a tool to generate Sec/Dictionary files for content discovery by scrapping GitHub for File/Folder Names and GET/POST & HTTP from PHP files. So far its examined 5,256,950 files from 39069 repositories, check the results https://github.com/adamtlangley/gitscraper …
#BugBounty#bugbountytipsTampilkan utas iniTerima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan -
Nguyen The Duc me-Retweet
One more to the pocket : CVE-2020-0901 - TALOS-2020-1015 Microsoft Office Excel s_Schema Code Execution Vulnerability https://talosintelligence.com/vulnerability_reports/TALOS-2020-1015 …
Terima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan -
Terima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan
-
I and my teammate really happy to share our latest research / doing bug bounty about WAF exploit / bypass. This is a popular WAF application from a vendor in Vietnam, hope you like it
 .
.
#bugbountytip#bypass#waf#pentest https://hackemall.live/index.php/2020/05/12/web-application-firewall-exploit-if-you-cannot-protect-yourself-who-can-you-protect/ …pic.twitter.com/sUjnHgjme9 Terima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan
Terima kasih. Twitter akan menggunakan ini untuk membuat timeline Anda lebih baik. BatalkanBatalkan
Pemuatan tampaknya berlangsung agak lama.
Twitter sedang kelebihan beban atau mengalami sedikit masalah. Coba lagi atau kunjungi Status Twitter untuk informasi lebih lanjut.


 | Security Researcher | Sr. Security Engineer | CTF player
| Security Researcher | Sr. Security Engineer | CTF player 





















